
The OWASP Top 10 is a globally recognised awareness standard for web application security, maintained by the Open Worldwide Application Security Project (OWASP). It identifies the ten most critical security risks that threaten modern applications, from access control weaknesses to software supply chain failures.
More than a checklist, the OWASP Top 10 acts as a practical guide for secure development. It helps developers and engineers understand where vulnerabilities emerge and how to design systems that prevent them from the outset.
Each edition is grounded in real-world data and community expertise, drawing from vulnerability databases, penetration testing reports, and global surveys to reflect current attack patterns.
For teams adopting DevSecOps or aligning with frameworks like ISO 27001, PCI DSS, or NIST SSDF, the OWASP Top 10 provides a clear foundation for embedding security by design into every stage of the software lifecycle.
In essence, it’s a shared language for building resilient, trustworthy applications, one that keeps pace with how technology and threats continue to change.
This 2025 version introduces new categories, redefines existing ones, and places stronger emphasis on secure design, supply chain integrity, and real-world misconfigurations.
If your team still operates around the OWASP Top 10 2021 framework, now is the time to bring your practices up to date, ensuring your applications remain secure in today’s environment of cloud-native architectures, API-driven systems, automated CI/CD pipelines, and AI-assisted development.
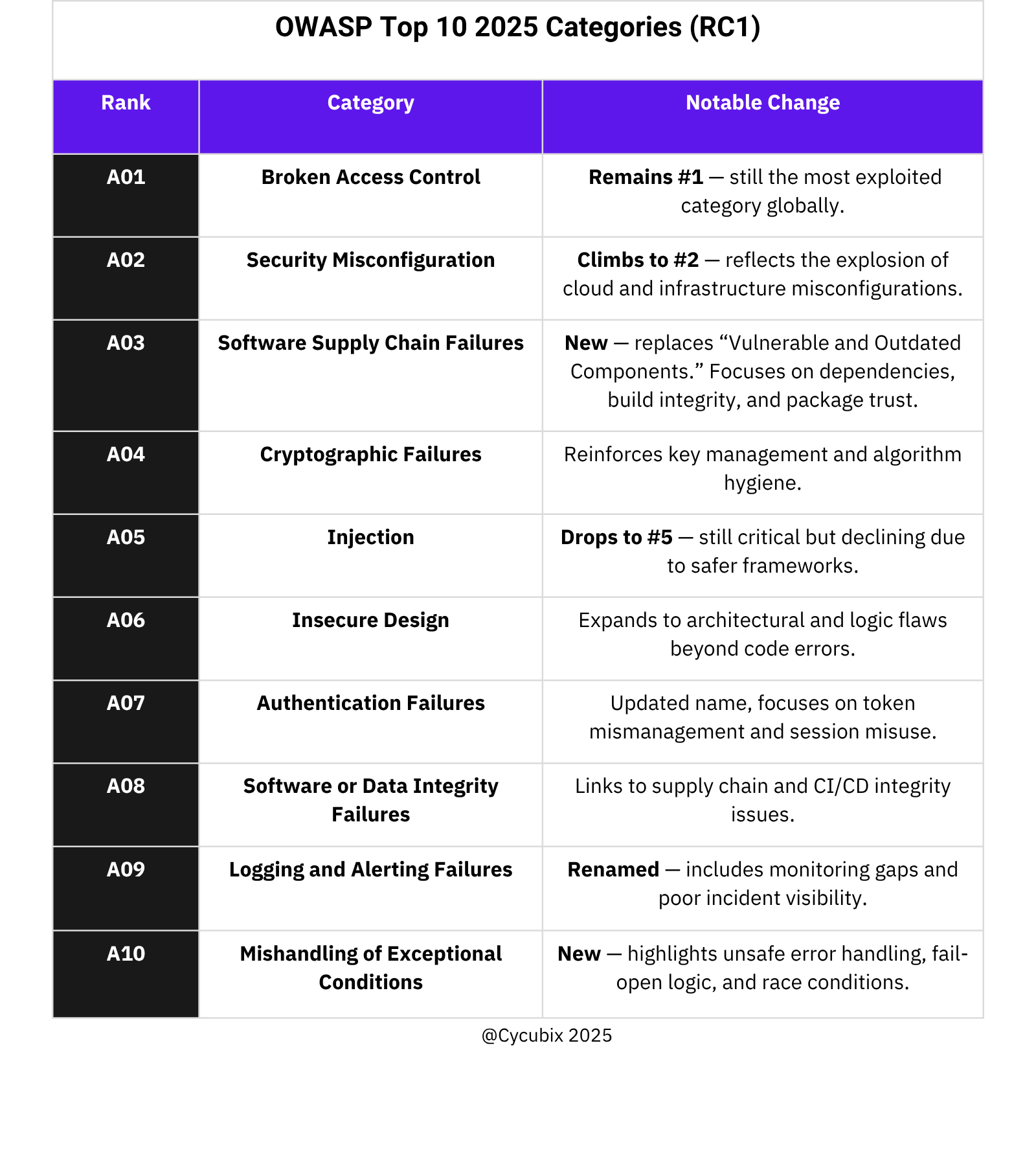
(Source: OWASP Top 10 2025 Introduction)
Default credentials, open S3 buckets, exposed Kubernetes dashboards — misconfiguration is no longer an operational mistake; it’s an existential risk.
Action: Adopt configuration-as-code reviews, automate drift detection, and apply least privilege everywhere.
“Vulnerable Components” wasn't enough. The 2025 version recognises that how software is built and distributed can be just as dangerous as what is in the code.
Action: Implement dependency signing, SBOM tracking, and pipeline integrity checks.
Security can’t be bolted on at the end. OWASP Top 10 2025 expands on Insecure Design to address Threat Modeling, architecture, and systemic weaknesses.
Action: Embed security design reviews in every project phase, not after deployment.
This new category targets unsafe error handling that exposes stack traces or leaves systems in inconsistent states.
Action: Validate all error-handling logic and ensure applications fail safe, not open.
The renamed Logging and Alerting Failures reflects how poor observability continues to hinder detection and response.
Action: Unify logging across environments and automate alert triage.
1. Perform a Gap Analysis: Map your current SDLC controls to the 2025 categories. Identify weak coverage in supply chain, design, and exception handling.
2. Update Your Secure Development Framework
3. Train and Empower Your Developers: Equip teams with hands-on secure coding training aligned with OWASP Top 10 2025. Move beyond awareness to practical skill.
4. Modernise Your Metrics: Measure maturity by tracking for example:
The OWASP Top 10 2025 isn’t just an iteration, it’s a recalibration of what secure software means in a world of cloud-native systems, interconnected APIs, and automated pipelines. The industry’s focus has shifted from code vulnerabilities to systemic integrity.
It’s about designing for resilience, building with integrity, and enabling teams to anticipate risks before they become incidents.
At Cycubix, we help development and engineering teams achieve this mindset, translating frameworks like the OWASP Top 10 into practical, day-to-day security practices that strengthen code, systems, and people.
→ Explore our hands-on Application Security and Secure Coding Training or contact us to build security-first development teams that grow fearless.